It is getting major to use cloud service to store source code but there are still many cases to build infrastructure in our own network. It is not only for company but also for personal project. I will try to build build-infrastructure with docker containers. Since necessary components are already in Docker-Hub we should easily be able to establish and use it.
What I use for this purpose is following.
- Gogs – open source Git service
- Jenkins – open source automation server
- registry – To have local Docker-Hub
Preparation of docker-compose file
I specified fixed version for each image because I don’t want to get them updated automatically. This definition is very simple. Since I mounted host directory to the container data is stored in the host directory. If we want to make a backup what we need to do is just to copy the directories.
version: "3.7"
x-labels: &infra-net
networks:
- infra-net
services:
gogs:
image: gogs/gogs:0.12.3
ports:
- "3000:3000"
volumes:
- ./gogs/data:/data
<<: *infra-net
registry:
image: registry:2.7.1
ports:
- "5000:5000"
volumes:
- ./registry/data:/data
- ./registry/config.yml:/etc/docker/registry/config.yml
<<: *infra-net
jenkins:
image: jenkins/jenkins:2.263.1-lts-slim
ports:
- "8080:8080"
- "50000:50000"
volumes:
- ./jenkins/home:/var/jenkins_home
<<: *infra-net
networks:
infra-net:
name: infra-netLet’s start it.
cd build-dev-infrastructure
docker-compose up -dSetting for Gogs
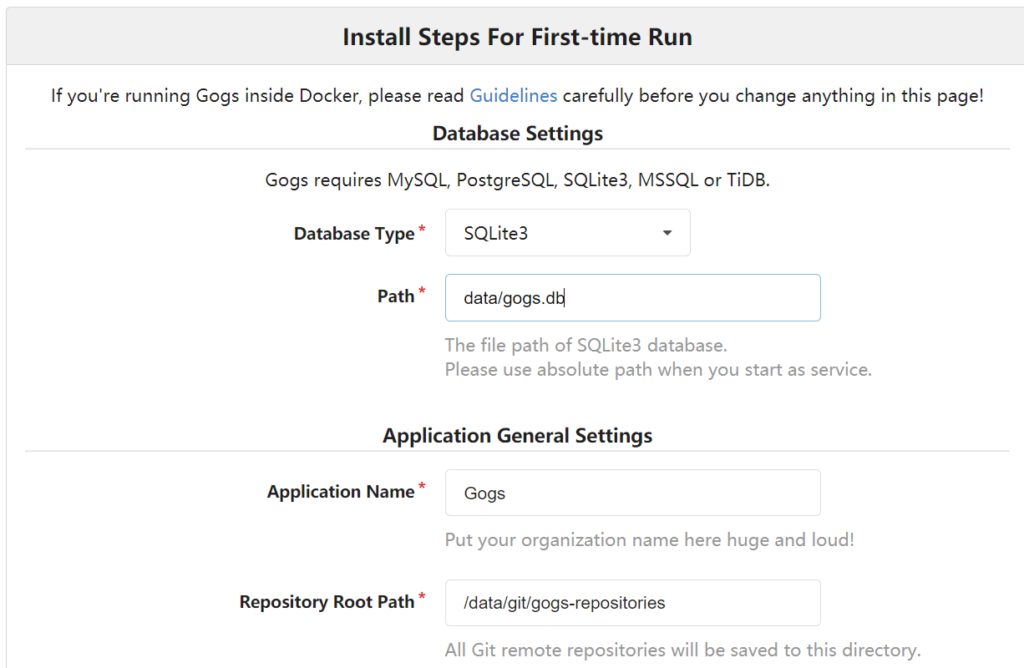
We can setup Gogs quickly. Browse to http://localhost:3000 and we can see the UI for the setting. PostgreSQL is selected as default database but it fails to proceed because it is not defined in this docker compose file. If you want to use it you need to add it yourself. If you don’t want to do it you can select SQLite3 instead. For the first access, we need to create new account and sign in. You can check Gogs manual if you want to know how to set up.
Setting for Jenkins
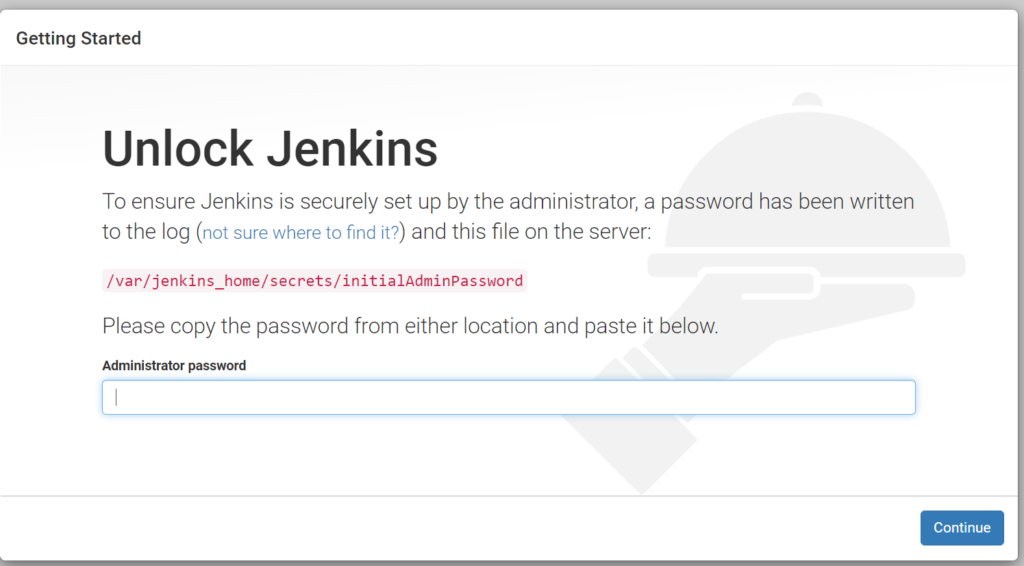
It takes a while to start Jenkins. Jenkins shows following for the first time. We need to copy the password from ./jenkins/home/secrets/initialAdminPassword and paste it here.
After this, we need to select which plugins to install. Select what you want and install them. If we already know which plugins there are and which plugins are useful we can package them all into the Docker image. If you manage them in git repository you can do it.
Push a docker image to local registry
Since we set the port to 5000 we can access to the local registry by localhost:5000. Let’s try to push a image to it.
Firstly let’s add a tag to a target image.
$ docker image ls alpine
REPOSITORY TAG IMAGE ID CREATED SIZE
alpine latest d6e46aa2470d 7 months ago 5.57MB
$ docker tag alpine:latest localhost:5000/my-alpine
$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
alpine latest d6e46aa2470d 7 months ago 5.57MB
localhost:5000/my-alpine latest d6e46aa2470d 7 months ago 5.57MBNew image is created as localhost:5000/my-alpine. The first part is to indicate where the registry is. Let’s push it.
$ docker push localhost:5000/my-alpine
Using default tag: latest
The push refers to repository [localhost:5000/my-alpine]
ace0eda3e3be: Preparing
ace0eda3e3be: Mounted from alpine
latest: digest: sha256:d7342993700f8cd7aba8496c2d0e57be0666e80b4c441925fc6f9361fa81d10e size: 528Then, remove the image from local machine and pull it from local registry.
$ docker image remove localhost:5000/my-alpine
Untagged: localhost:5000/my-alpine:latest
Untagged: localhost:5000/my-alpine@sha256:d7342993700f8cd7aba8496c2d0e57be0666e80b4c441925fc6f9361fa81d10e
$ docker image remove alpine
Untagged: alpine:latest
Untagged: alpine@sha256:c0e9560cda118f9ec63ddefb4a173a2b2a0347082d7dff7dc14272e7841a5b5a
$ docker pull localhost:5000/my-alpine
Using default tag: latest
latest: Pulling from my-alpine
Digest: sha256:d7342993700f8cd7aba8496c2d0e57be0666e80b4c441925fc6f9361fa81d10e
Status: Downloaded newer image for localhost:5000/my-alpine:latest
localhost:5000/my-alpine:latest
$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
localhost:5000/my-alpine latest d6e46aa2470d 7 months ago 5.57MBIt works. The default registry is original docker hub and it seems not to be able to change it because it breaks the basic concepts that a user can establish exactly the same environment wherever he is. If the default registry changes a user can pull a old image from local registry. This is just a trial to establish necessary environment. In Docker doc, it says that a user must to use TLS for the connection.
Warning: These first few examples show registry configurations that are only appropriate for testing. A production-ready registry must be protected by TLS and should ideally use an access-control mechanism. Keep reading and then continue to the configuration guide to deploy a production-ready registry.
docker docs – Deploy a registry server
Add those additional features if you want to establish the environment in your own network.
Conclusion
It was very easy to establish the three by using docker. What I did was mostly to get images from docker hub. If we want to establish Jenkins and local registry we need to do additional work for them because we probably wants to install useful plugins.





Comments